# The Unsung Powerhouse of Cybersecurity: Excel Reimagined
Written on
Chapter 1: The Uncelebrated Star
This article shines a light on an often-overlooked yet essential tool in the cybersecurity realm!
Professionals in cybersecurity often mention that one of the most exciting aspects of their work is engaging with various innovative applications and software. The cybersecurity landscape is rich with tools, ranging from high-end enterprise solutions costing millions to open-source options available for free. However, amidst this plethora of software, one tool has been consistently relied upon by billions of cybersecurity experts for decades: Microsoft Excel. It’s high time we acknowledge its vital role.
Let me present three compelling reasons why this spreadsheet software deserves more recognition than it typically receives.
Section 1.1: Reason One — Excel: The Original SIEM
Security Information and Event Management (SIEM) solutions gather data across your environment and trigger alerts in real-time upon detecting suspicious activities. Despite the advanced capabilities of these systems, nothing compares to the effectiveness of inputting raw data into Excel and filtering through it for specific issues during incidents. Many analysts, despite having access to state-of-the-art tools, still resort to Excel for in-depth analysis when faced with particular challenges. Its blend of simplicity and robust functionality makes it a preferred choice for navigating extensive datasets.
Section 1.2: Reason Two — VLOOKUP: The Speed Demon
In the fast-paced world of security incidents, speed is of the essence. When you need to swiftly locate very specific data within a vast dataset, the remarkable VLOOKUP function in Excel can outperform many commercial cybersecurity tools. It provides a rapid method for cross-referencing data, equipping you with vital insights necessary for making critical decisions.
Subsection 1.2.1: Reason Three — PivotTables vs. Machine Learning
Machine Learning is currently a hot topic, touted for its ability to provide insights into large volumes of security data. Many cybersecurity products flaunt the "Powered by AI" or "Powered by Machine Learning" label. However, if you have utilized Excel’s PivotTable feature, you may have already been extracting valuable insights from your security data. PivotTables allow users to summarize, analyze, and manipulate large datasets, transforming them into actionable information. With the right skills, you can uncover hidden patterns, relationships, and trends that might otherwise remain unnoticed!
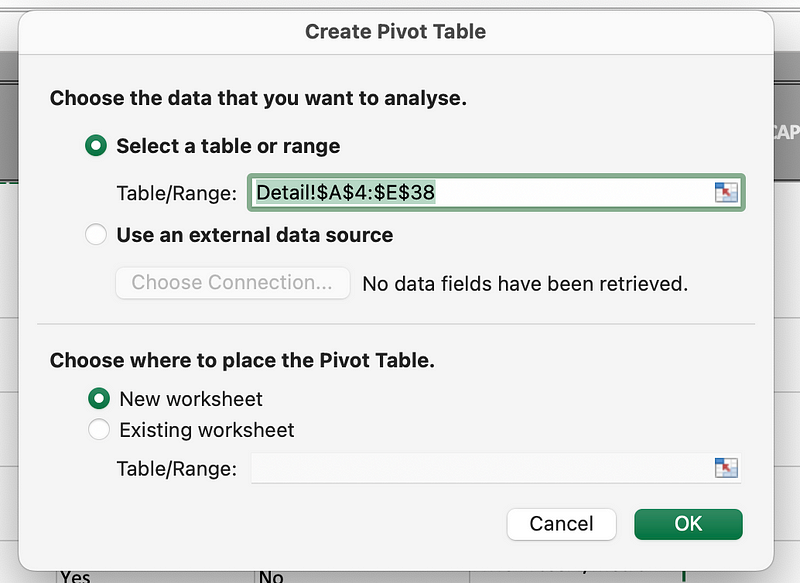
Source: Author
These three reasons barely scratch the surface; professionals ranging from Chief Information Security Officers (CISOs) to cybersecurity analysts utilize Excel in various capacities. This article aims to highlight the immense value of this remarkable tool. Although it may lack the glitz of high-cost cybersecurity solutions, its straightforwardness is what makes it indispensable for any expert in the field.
So, this year, commit to enhancing your Excel skills to harness the full potential of this incredible tool!

Taimur Ijlal is an award-winning leader in information security, boasting over 20 years of international experience in cybersecurity and IT risk management within the fintech sector. Connect with Taimur on LinkedIn or explore his YouTube channel, "Cloud Security Guy," where he regularly shares insights on Cloud Security, Artificial Intelligence, and general career advice in cybersecurity.
Don’t miss out on my free eBook that offers tips on boosting your earnings in cybersecurity!
You can gain full access to every story on Medium for just $5/month by signing up through the link below:
Read all articles by Taimur Ijlal (and thousands of other writers on Medium). Your membership directly supports...